.webp)
Content
Today’s digital infrastructure is evolving faster than most security teams can keep up. Every new cloud service, API integration, open-source component, or SaaS subscription expands the organization's attack surface, often without full visibility or control over it. What begins as innovation quickly turns into risk: misconfigured assets, forgotten environments, over-permissioned accounts, and unsecured endpoints all become easy entry points for attackers.
In fact, by 2024, over 80% of organizations reported at least one cloud-related security incident, many traced back to shadow IT, mismanaged identities, or unmonitored assets. Cybercriminals know they don’t need to break down the front door when they can just find an unlocked side window.
In this landscape, Attack Surface Reduction (ASR) is no longer just a good practice, it’s a foundational strategy. It shifts organizations from reactive defense to proactive resilience by:
- Eliminating unnecessary exposures
- Automating access and security policies
- Embedding secure-by-default principles in development and operations
If you don’t actively manage your attack surface, threat actors will. In this blog, we’ll walk through 10 essential ASR best practices that help reduce digital exposure, secure your digital environment, and empower your teams to innovate securely.
What Is an Attack Surface?
An attack surface refers to the comprehensive set of points within your digital environment where an attacker could attempt to gain access. Think of your attack surface as everything in your organization that’s exposed to the outside world, intentionally or not. It includes your websites, cloud servers, APIs, user endpoints, third-party integrations, IoT devices, and even abandoned or forgotten assets, such as old development environments or unused SaaS subscriptions. If it’s connected and can be accessed, scanned, or exploited, it’s part of your attack surface.
The problem? Most organizations don’t realize just how big their attack surface is. With the rapid adoption of cloud, remote work, and microservices, things get spun up quickly and often without proper tracking. Over time, this creates a patchwork of exposures, some obvious, many invisible.
What Is an Attack Vector?
If the attack surface is where attackers can gain entry, an attack vector is how they actually gain access.
An attack vector is the method or pathway a threat actor uses to exploit a vulnerability and gain unauthorized access. It could be a phishing email, a misconfigured S3 bucket, an unpatched system, a compromised password, or even a rogue API call. Some are technical, while others are social (such as tricking an employee into clicking a malicious link).
Here’s the catch: As your digital operations grow, so does the number of attack vectors. Each misstep in access control, software update, or asset inventory creates another possible route for attackers.
Understanding your attack vectors helps you build layered defenses. Because attackers don’t care how they gain access as long as they succeed.
Proven Strategies and Best Practices for Attack Surface Reduction
Attack Surface Reduction isn’t just about cutting down exposure; it’s about building smarter, scalable security from the ground up. It helps block common threats, such as malware and exploits, by enforcing secure defaults, scanning code and containers, and eliminating risky behaviors before they reach production.
ASR also limits damage from potential breaches by tightening access, isolating workloads, and preventing lateral movement. With real-time protections like phishing filters, token scanning, and stronger identity controls (think SSO, MFA), your defenses become sharper where they matter most.
Additionally, by integrating these policies into your CI/CD pipeline, ASR automates security, scales with your growth, and doesn't slow teams down.
1. Automate Security Testing Within Your Development Pipeline
Reducing your attack surface starts with knowing exactly what’s being deployed, and that’s only possible by integrating security checks directly into your CI/CD pipeline. A CI/CD pipeline (Continuous Integration/Continuous Deployment) is an automated process that helps developers build, test, and deploy code quickly. It powers modern software delivery but without built-in security, it can introduce risks as fast as it delivers features.
For instance, automated static analysis (ASA) tools catch unsafe coding patterns and logic flaws before they reach production, while dependency scanning, including indirect libraries and container base images, helps prevent vulnerable components from slipping in unnoticed. Secret detection tools flag hardcoded credentials, such as API keys, early, thereby closing a common attack vector.
But static tools alone aren’t enough. Continuous penetration testing simulates attacker behavior on your evolving codebase and infrastructure, which uncovers risks that automated scans may miss. The real power lies in treating security testing with the same discipline as functional tests, blocking deployments for critical issues while allowing flexibility on minor findings.
When you integrate multiple scanners into a streamlined, policy-driven workflow, security becomes an integral part of your daily development rhythm, reducing your attack surface without slowing innovation.
2. Minimize Digital Exposure: Ports, Services & Code
Every open port, running service, and piece of exposed code expands your attack surface, each one a potential entry point for attackers. Open ports, such as 21 (FTP) and 445 (SMB), are frequently targeted due to their history of vulnerabilities and are commonly scanned by attackers seeking easy entry.
For example, a recent Specops report analyzed FTP brute-force attempts over 30 days, uncovering commonly used passwords and reinforcing the risk posed by 133 million compromised credentials. Leaving such ports open without strict justification and controls invites continuous attack attempts. Closing unnecessary ports isn’t just about shutting doors it’s about eliminating entire classes of risk that attackers automatically scan for.
Unused services and legacy applications often linger unnoticed, quietly introducing exploitable flaws and increasing system complexity. These “forgotten” assets often lack timely patching and monitoring, making them vulnerable to exploitation. Hardening your environment means a rigorous, ongoing process of stripping out defaults, removing outdated software, and tailoring configurations to your actual operational needs because every service running is another layer to defend.
This disciplined approach doesn’t just lower risk, it builds a foundation where security becomes part of everyday operational hygiene.
3. Apply Zero Trust and Least Privilege to Cloud IAM
In today’s complex cloud environments, identity is the new security perimeter. The Zero Trust Architecture (ZTA) model assumes that a breach is inevitable or has already occurred, and therefore continuously verifies and limits access to only what is necessary.
Rather than trusting users or systems by default, Zero Trust requires strict access controls combined with ongoing monitoring for any anomalous or malicious activity.
The principle of Least privilege means granting users and services only the permissions they truly need to perform their tasks. This limits potential damage if credentials are compromised and reduces your overall attack surface. Combine least privilege with Zero Trust by continuously evaluating access requests in real time, considering:
- Who is asking for access
- What resource is being targeted
- Where and how the request is coming from
- Is the behavior normal or suspicious
By adopting Zero Trust and least privilege together, your cloud environment becomes far more resilient, assuming a breach but minimizing impact and increasing detection speed.
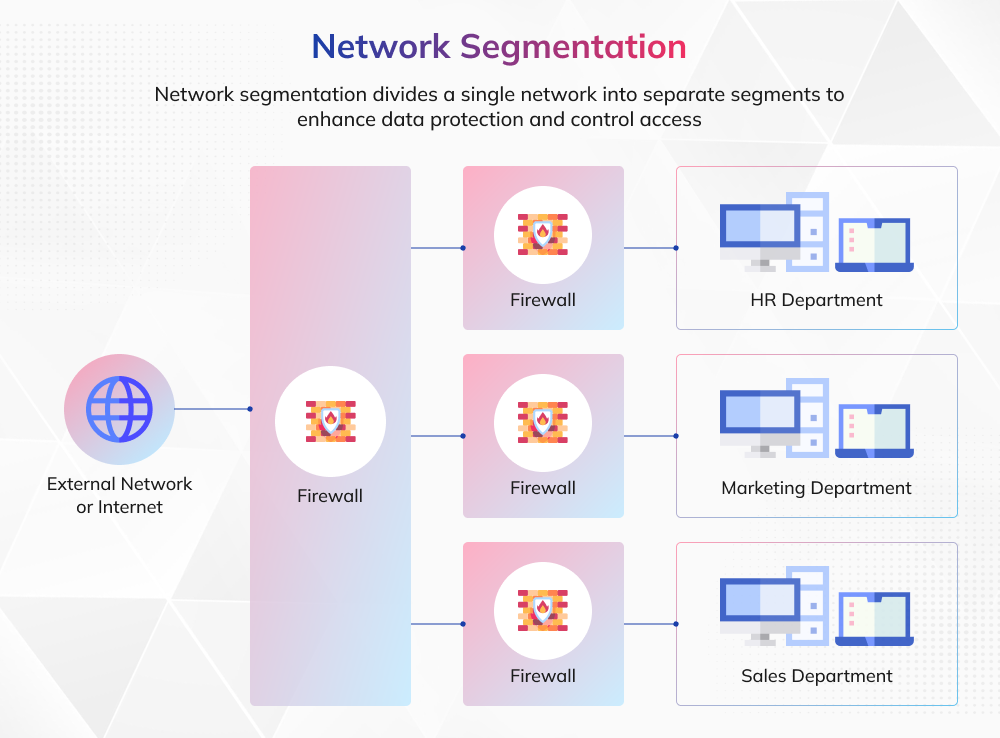
4. Segment Networks at Multiple Levels to Limit Exposure
Network segmentation is one of the most effective ways to reduce your attack surface and limit damage in the event of a breach. Studies show that organizations using microsegmentation can reduce lateral movement, drastically slowing attackers once they get inside.
Segmentation means dividing your network into smaller, isolated zones. Begin with broad segments, such as separating user devices from critical servers, and then apply microsegmentation to enforce fine-grained, identity-based security controls across workloads, applications, and users.
Unlike traditional segmentation that primarily manages perimeter (north-south) traffic, microsegmentation focuses on (east-west traffic patterns) the lateral movement that attackers exploit after an initial breach. By isolating workloads and restricting communication paths to only what is explicitly allowed, microsegmentation prevents attackers from freely moving within your environment. This granular isolation limits exposure, contains breaches to specific segments, and ensures that even if one workload is compromised, others remain protected.
This approach prevents attackers from freely moving east-west within your environment, a common tactic in advanced breaches.
By layering traditional segmentation with microsegmentation, you create multiple checkpoints that attackers must bypass. This containment strategy significantly limits exposure and buys your security teams valuable time to detect and respond before critical assets are compromised.
In modern cloud-native environments, where IP-based controls often fall short, microsegmentation enables dynamic, context-aware policy enforcement. When combined with Zero Trust principles, it transforms your network into a tightly controlled environment that adapts in real-time to risk, significantly reducing the exploitable surface area.
To strengthen this layered defense, consider pairing segmentation with advanced data fragmentation. This technique disperses sensitive data into cryptographically separated fragments across multiple storage locations, making it nearly impossible for attackers to reconstruct usable information even if they breach part of your system. It ensures that compromising one vault or credential doesn’t expose full datasets.
5. Integrate Continuous Security Testing Into DevOps
Bringing security into your DevOps pipeline early and often is one of the most effective ways to reduce your attack surface. When you integrate automated checks, such as code scanning, dependency reviews, and secrets detection, directly into your build and deployment process, you catch problems before they become costly headaches.
Making these security checks a non-negotiable step means that risky code doesn’t make it to production, without slowing down your developers. It helps everyone build safer software, faster.
In short, it integrates security into your everyday workflow, making it smooth, effective, and developer-friendly.
6. Protect Web Applications with Advanced Filtering
Web applications are the primary targets for attackers exploiting vulnerabilities such as injection attacks, credential stuffing, and automated bot traffic. Deploying a Web Application Firewall (WAF) along with bot management solutions is a must to defend these entry points.
By implementing these measures, you establish a dynamic defense that filters out malicious activity, protects sensitive data, and maintains the security and availability of your web applications.
7. Automate Threat Detection and Incident Response Workflows
Automating threat detection and incident response is critical in today’s world, where attackers can exploit vulnerabilities in minutes. Research shows that organizations with automated response capabilities reduce their mean time to respond (MTTR) by 70-80%, thereby limiting the impact of breaches.
By centralizing telemetry from endpoints, cloud platforms, and identity services, security teams get a holistic view to detect real threats in the noise. SOAR tools then automate workflows, such as alert triage, containment, and remediation, removing manual bottlenecks and human error during high-pressure incidents.
This not only speeds up response but ensures consistent and repeatable actions that improve over time with refined playbooks. Ultimately, automation transforms incident response from reactive firefighting into a proactive, scalable defense strategy, allowing teams to focus on strategic threat hunting and continuous improvement.
8. Foster a Security-Aware Workforce Through Ongoing Training
People are often the easiest target for attackers and the hardest to predict. In fact, over 74% of data breaches involve some form of human error or manipulation, like phishing or social engineering. That’s why continuous, tailored security training isn’t just nice to have—it’s a must.
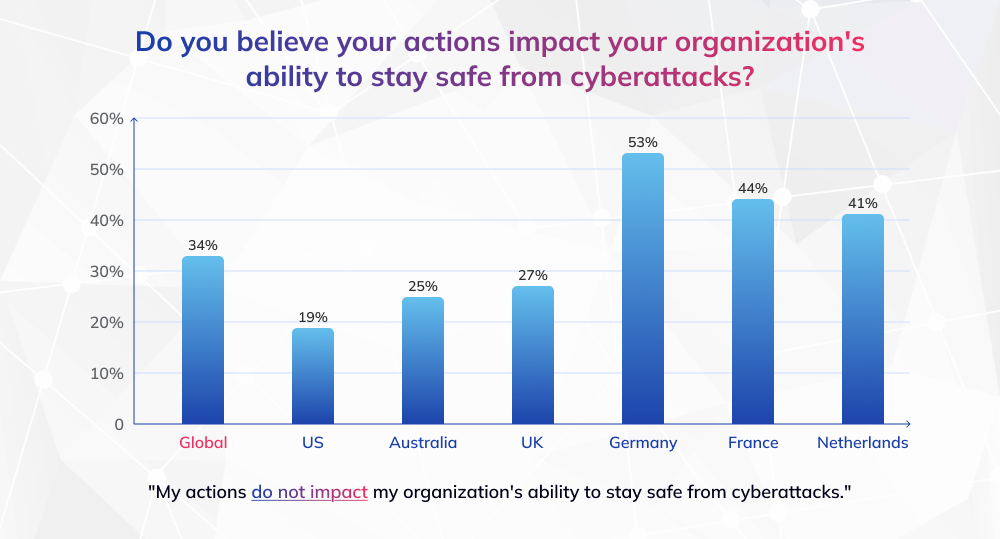
Regular training helps employees recognize the tricks hackers use and understand how their daily actions impact the company’s security. When employees feel informed and empowered, they become active defenders rather than weak links. Many employees don't believe their actions impact their organization's ability to stay safe from cyberattacks.
This type of ongoing education reduces risky behaviors, such as clicking on suspicious links or using weak passwords, which can otherwise open doors for attackers. Building a security-first culture where security is everyone’s job creates a powerful first line of defense, dramatically shrinking your human attack surface and making your whole organization safer.
9. Remove Unused and Exposed APIs
APIs have become the backbone of modern applications and cloud services, but they also dramatically expand your attack surface, especially when old or undocumented APIs remain exposed. Research indicates that over 99% of organizations have at least one forgotten or unused API still accessible, which poses significant security risks.
These legacy or internal-only APIs often lack proper authentication, rate limiting, and logging, making them prime targets for attackers seeking to exploit sensitive data or gain unauthorized access. Attackers also employ techniques such as GraphQL introspection and automated scanning to uncover hidden endpoints that leak sensitive information.
Real-World Breaches That Exposed the Cost of a Widening Attack Surface
When companies don’t keep their attack surface in check, the results can be costly. Here are a couple of real-world examples of how quickly things can go wrong when security gaps are left unaddressed:
Can Outsourcing Help Reduce the Attack Surface?
Keeping your attack surface safe in today’s fast-changing digital world is a significant task and can be quite challenging. With so many cloud systems, apps, and constant changes, it’s easy for internal teams to feel overwhelmed. That’s why many companies choose to outsource this work.
Invensis offers expert cybersecurity services designed to keep your digital world safe and sound. Here’s how they can help:
- 24/7 Monitoring: They continually monitor your network and systems to promptly identify any potential weaknesses or unusual activity.
- Vulnerability Management: Invensis identifies and fixes security gaps before attackers can exploit them.
- Cloud & Endpoint Security: They secure your cloud setups and all devices connected to your network, reducing entry points for hackers.
- Policy Enforcement: They help establish and maintain robust security protocols to ensure everyone in your company adheres to best practices.
- Incident Response: If something suspicious occurs, Invensis acts promptly to contain and resolve the issue, minimizing potential damage.
- Compliance Support: They help you meet key cybersecurity standards and regulations, thereby avoiding fines and building customer trust.
By partnering with Invensis, you gain a proactive team that handles your security, allowing your in-house staff to focus on growing your business without worrying about cyber threats.
Conclusion
Every new app, device, or cloud service adds potential risks, making attack surface management a top priority. Utilizing smart strategies, such as regular security checks, segmenting your network into smaller parts, and granting access only to those who truly require it, can make a significant difference.
But let’s face it, managing all this can quickly become overwhelming. That’s where trusted partners like Invensis step in; they keep a constant eye on your security, spot trouble early, and let your team focus on what they do best. Taking these steps today means you’re not only protecting your business now but also building a safer, stronger future.
Frequently Asked Questions
Discover Our Full Range of Services
Click HereExplore the Industries We Serve
Click HereBlog Category
Related Articles

Optimize your store in 2026 with the best WooCommerce order management plugins. Automate order tracking, inventory, and customer service for success.
January 21, 2026
|

Find the leading accounting firms in Singapore trusted by businesses for audit, tax, and advisory services.
November 6, 2025
|

Explore the leading accounting firms in South Africa providing expert audit, tax, cloud accounting, and payroll services. Learn about their key features and unique offerings.
February 2, 2026
|
Services We Provide
Industries We Serve







.webp)
.webp)
.webp)