Content
Healthcare data breaches are no longer rare; they’ve become alarmingly common and more sophisticated. In the first quarter of 2026, over 650 security incidents were reported, exposing sensitive information of more than 32 million people. And the trend hasn’t slowed down. High-profile attacks, like the ransomware breach at Frederick Health Medical Group in April, put nearly a million patient records at risk.
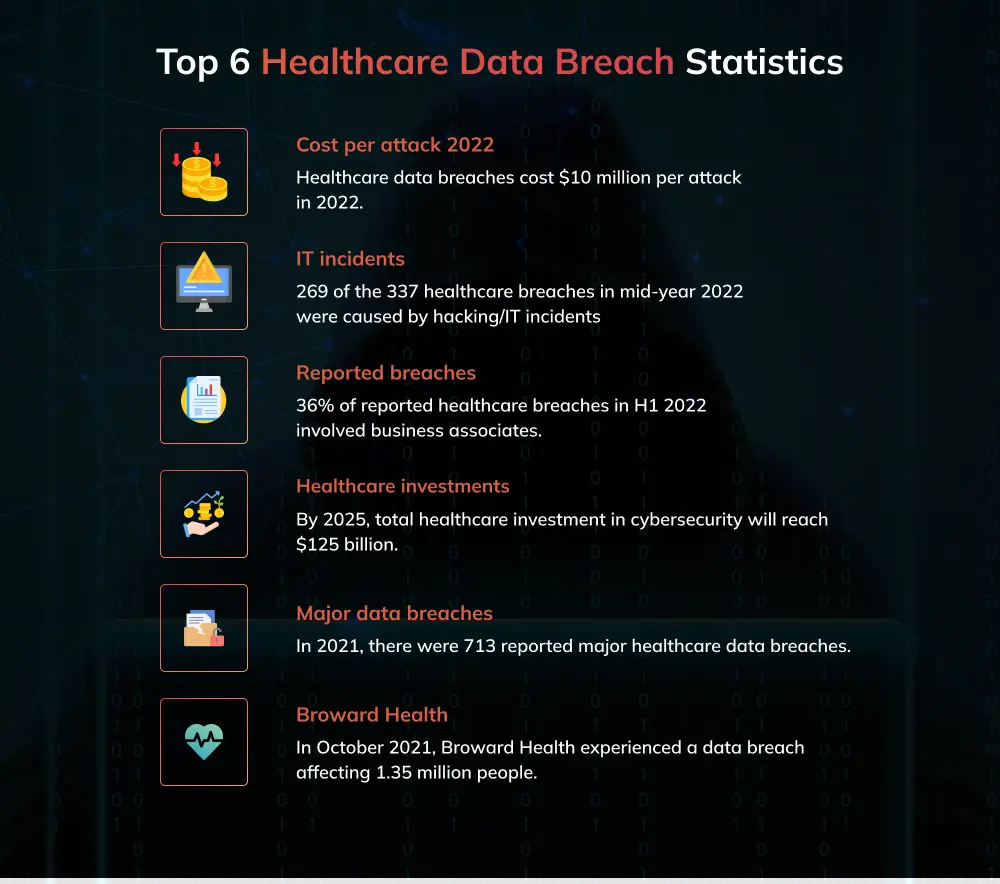
According to the 2024 IBM Cost of a Data Breach Report, healthcare breaches cost an average of $11.45 million per incident, the highest across all industries. In 2026, attackers are exploiting specific weaknesses in EHR (Electronic Health Record systems and outdated network architectures.
It’s not just the systems they’re after, it's the people. Cyber attackers are increasingly counting on human error, and when staff aren’t properly trained, even small mistakes can open the door to serious breaches.
In this article, we’ll explore the top healthcare cybersecurity threats backed by real cases and new tactics, plus practical steps to help you strengthen defenses and stay ahead.
Why Healthcare Data Is a Target for Cyber Attacks
Healthcare organizations consistently rank among the most targeted sectors for cyber attacks, and several concrete factors drive this:
1. Extremely Valuable and Sensitive Data
According to experts, your medical information is worth 40 times more than your credit card number in the black market. Patient records contain highly detailed personal, financial, and medical information. This data can be used for identity theft, insurance fraud, or even blackmail, making it far more valuable than typical personal data. Attackers know that stealing medical records can lead to long-term exploitation, which makes healthcare a lucrative target.
2. Complex and Diverse IT Systems
Nearly 73% of Healthcare providers rely on a patchwork of legacy systems, connected medical devices, and cloud platforms. This diversity creates numerous weak points in the network, many of which go unpatched or poorly managed. Cybercriminals exploit these gaps to gain unauthorized access.
3. Critical Need for Continuous Operation
Hospitals and clinics can’t afford downtime; any disruption to patient care can be life-threatening. This urgency means that healthcare organizations may prioritize restoring systems quickly over thorough security investigations, making them prime victims for ransomware attacks, where attackers demand payment for system recovery.
4. Limited Cybersecurity Investment and Resources
Compared to other sectors, healthcare often underinvests in cybersecurity infrastructure and skilled personnel. Many organizations lack comprehensive security programs or have insufficient budgets dedicated to continuous threat monitoring and employee training, increasing their vulnerability.
5. Expanding Digital Footprint with Emerging Technologies
The growth of telemedicine, Internet-connected medical devices, and cloud-based EHRs has significantly expanded the attack surface. Each new device or remote access capability introduces potential entry points for attackers and even increases the chances of a breach.
Top Cyber Threats to Healthcare Data in 2026
Now that we know about why hackers are targeting healthcare data, it’s high time to consider some of the top threats to medical data in 2026. Let’s talk about each one of them in detail:
1. Ransomware Targeting EHR Systems
Electronic Health Record (EHR) platforms remain a prime target for ransomware attacks due to their critical role in patient care. The World Health Organization rightly calls these incidents “life and death” matters, as compromised Electronic Health Record (EHR) systems can delay or block access to critical patient information.
Attackers leverage this to encrypt data and demand ransom payments, knowing providers face intense pressure to restore services rapidly. But paying the ransom isn’t a silver bullet.
One-third of ransom payments fail to unlock data, prolonging operational chaos. The 2023 Ascension breach highlights the significant impact, with over $130 million spent on recovery and nearly $900 million in lost revenue, resulting in patient care being forced onto fragile paper workflows for weeks.
These events highlight how attackers focus on EHRs not only for financial gain but also to maximize operational disruption, leveraging the urgency and complexity of healthcare workflows. Securing EHR systems with timely patching, backups, and incident response plans is now a non-negotiable defense.
2. Insider Threats and Credential Misuse
Insider threats in healthcare often arise because overworked staff and busy vendors juggle multiple tasks, leading to lapses in security hygiene. When employees are fatigued or distracted, they’re more likely to reuse weak passwords, fall for phishing emails, or inadvertently share login credentials. Social engineering tactics prey on this human vulnerability by mimicking trusted contacts or urgent requests, tricking users into revealing access details.
For example, Tesla recently faced a major breach when two former employees exposed sensitive data of over 75,000 people, showing how insider risks can cause serious harm if unchecked.
Vendors and third parties frequently require broad system permissions to perform their work. Without strict oversight, these privileges can be exploited either accidentally through negligence or deliberately by malicious insiders.
Attackers take advantage of this trusted access to move laterally within networks, bypass traditional defenses, and extract sensitive healthcare data.
3. Phishing and Social Engineering in Clinical Environments
Phishing is still one of the top cyber threats targeting healthcare, with attackers crafting highly tailored emails that mimic appointment reminders or lab report notifications to lure clinical staff. These convincing ploys exploit the high-pressure environment where quick decisions are routine, making staff more susceptible to clicking malicious links or sharing credentials.
Attackers are crafting highly tailored emails that mimic appointment reminders or lab report notifications to lure clinical staff. These convincing ploys exploit the high-pressure environment where quick decisions are routine, making staff more susceptible to clicking malicious links or sharing credentials.
A lack of ongoing cybersecurity training further compounds the vulnerability, leaving employees ill-prepared to spot sophisticated social engineering attacks.
4. Supply Chain and Third-Party App Exploits
Healthcare’s growing dependence on connected medical devices, AI diagnostic tools, and third-party software integrations broadens its attack surface. Each supplier or app introduced into the ecosystem presents potential vulnerabilities. Cybercriminals have increasingly targeted supply chains by compromising less-secure third-party vendors to infiltrate primary healthcare networks.
In 2026, healthcare’s reliance on an expanding network of connected devices, AI tools, and third-party software has created numerous indirect access points. Many vendors still operate with outdated security or lack strict oversight, providing cybercriminals with easier targets to breach. Attackers exploit trusted relationships between healthcare providers and these vendors to bypass traditional defenses, moving laterally across networks without immediate detection.
5. AI-Powered Attacks and Deepfakes
As healthcare adopts AI technologies, threat actors are also leveraging AI for malicious purposes. AI-powered attacks now include sophisticated deepfake audio and video that can impersonate healthcare staff to bypass authentication or manipulate patients.
Early 2024 saw the first reported incidents where attackers used AI-generated voice deepfakes to authorize fraudulent prescriptions or extract sensitive data remotely.
.webp)
By the end of 2026, with AI embedded in everything from patient care to even administrative tasks, these risks will have only grown. Remote work and digital interactions create more opportunities for AI-driven impersonation and manipulation.
To stay ahead, healthcare cybersecurity teams must adopt advanced AI-based detection tools that can spot synthetic voices and unusual behavior patterns, ensuring patient safety and data security in an environment where deception is becoming harder to detect.
6. Real-World Impacts of Healthcare Data Breaches
Healthcare data breaches have far-reaching consequences beyond regulatory fines. Patient trust erodes when sensitive health information is exposed, potentially affecting patients’ willingness to seek care or disclose crucial details. Treatment delays caused by locked systems during cyberattacks can threaten lives.
Recent breaches, such as the 2024 ransomware attack on Change Healthcare, disrupted claims processing nationwide, illustrating how attacks ripple through the healthcare ecosystem. Compliance penalties also add financial strain on already resource-constrained providers. These impacts underscore the urgent need for robust cybersecurity best practices that protect Healthcare Data and ensure continuity of care.
Case Study: Targeted Ransomware in Healthcare - Two Lessons from 2026
Securing Healthcare Data in 2026: Recommendations
Securing Healthcare Data in 2026 requires healthcare organizations to move beyond conventional defenses and adopt intelligent, adaptive strategies that align cybersecurity with patient care priorities.
- Leverage AI for Proactive Threat Detection and Response:
Healthcare environments generate an overwhelming amount of data every minute, from patient records and device logs to network activity, making manual monitoring unfeasible. AI-driven systems act as tireless digital sentinels, detecting subtle deviations in user behavior or unusual traffic patterns that often escape human notice. These early signals provide security teams with precious lead time sometimes days to investigate and neutralize threats before they can compromise sensitive data or disrupt critical operations. As AI tools become more sophisticated, healthcare organizations that harness them effectively gain a crucial advantage against increasingly stealthy and automated attacks.
- Adopt Zero Trust with Fine-Grained Network Segmentation:
In healthcare, trust can be a dangerous assumption. Whether it’s a compromised device, an over-privileged user, or an insider mistake, breaches can happen anywhere. Zero Trust architecture forces continuous verification never assuming safety based solely on location or credentials. Breaking networks into tightly controlled segments means that even if attackers breach one area, their ability to move laterally and cause harm is sharply curtailed.
For hospitals, this means vital systems like Electronic Health Records and life-support devices remain shielded, helping to maintain patient care continuity during cyber incidents. This approach isn’t just technical it’s about recognizing that healthcare’s critical mission demands layers of protection where every access point is treated as untrusted until proven otherwise.
- Implement Continuous, Risk-Based EHR Security Hardening:
Healthcare systems are complex and constantly evolving. A one-time patch is insufficient when new vulnerabilities emerge daily. A dynamic, risk-based approach means continuously ingesting the latest threat intelligence while monitoring internal system health and configurations in real time. This allows security teams to prioritize actions based on actual risk rather than static checklists. Critical patches and access reviews are automated and accelerated, closing gaps before attackers can exploit them.
For healthcare providers, this approach directly translates into stronger protection for the most sensitive and essential Healthcare Data, minimizing both breach risk and operational disruption.
- Build a Security-First Culture to Reduce Human Error:
Behind every piece of technology is a person, and in healthcare, the stakes couldn’t be higher. Overworked staff under immense pressure are more prone to errors that cybercriminals exploit clicking phishing links, mishandling sensitive data, or inadvertently sharing credentials.
Addressing this requires more than a one-time training session; it demands ongoing, role-specific education that acknowledges the realities of clinical workflows and human psychology.
By embedding cybersecurity awareness into everyday routines, empowering staff with practical tools, and fostering a culture where vigilance is shared and rewarded, organizations transform potential vulnerabilities into their strongest line of defense. In 2026, this human element remains the cornerstone of any resilient healthcare cybersecurity strategy.
How Invensis Can Help Strengthen Healthcare Cybersecurity to Protect Healthcare Data
Healthcare organizations today operate in a landscape marked by increasingly sophisticated and persistent cyber threats. Protecting sensitive Healthcare Data and ensuring uninterrupted clinical operations demand a comprehensive, multi-layered cybersecurity strategy grounded in advanced technology and strategic risk management.
- Malware Protection: Deploying advanced endpoint security solutions that proactively detect and block malware targeting critical healthcare systems such as EHR and telehealth platforms, preventing compromise before it occurs.
- Ransomware Defense: Implementing multi-layered defenses that integrate real-time threat intelligence, strict network segmentation, and AI-driven anomaly detection to prevent ransomware infiltration and enable rapid containment if attacks occur.
- Phishing Prevention: Combining targeted, role-specific cybersecurity training with simulated phishing exercises and robust email filtering systems to reduce risks from credential theft and initial compromise vectors.
- Social Engineering Mitigation: Educating personnel to recognize and resist sophisticated social engineering tactics, supported by clear policy frameworks and well-defined incident response procedures.
- DDoS Mitigation: Employing scalable defense mechanisms to ensure healthcare infrastructure remains resilient against distributed denial-of-service attacks, preserving the availability of critical digital services.
- Advanced Persistent Threat (APT) Defense: Maintaining continuous monitoring and threat hunting capabilities to detect and neutralize stealthy, prolonged cyber intrusion attempts targeting healthcare data assets.
- Insider Threat Management: Utilizing behavioral analytics and strict access controls to identify and mitigate risks originating from trusted insiders.
- Zero-Day Exploit Protection: Leveraging proactive vulnerability management combined with AI-enabled threat detection to defend against emerging and previously unknown exploits before they can be weaponized.
A strategic approach that integrates these capabilities, aligned with regulatory compliance and organizational risk tolerance, is essential. Coupled with fostering a security-first culture that empowers healthcare personnel, this framework strengthens defenses, reduces attack surfaces, and ensures the continuity of safe, high-quality patient care amid an evolving threat environment.
Conclusion
The healthcare sector faces complex and evolving cyber threats in 2026, with ransomware, insider risks, phishing, supply chain vulnerabilities, and AI-powered attacks at the forefront. Protecting Healthcare Data requires proactive security postures that combine advanced technology with human vigilance.
Collaboration with vendors and ongoing investment in cybersecurity are essential to safeguard sensitive health records and maintain patient trust. Only through comprehensive, adaptive defenses can healthcare organizations effectively navigate the cyber risks that threaten patient safety and care delivery.
FAQs
Discover Our Full Range of Services
Click HereExplore the Industries We Serve
Click HereBlog Category
Related Articles

Optimize your store in 2026 with the best WooCommerce order management plugins. Automate order tracking, inventory, and customer service for success.
January 21, 2026
|

Find the leading accounting firms in Singapore trusted by businesses for audit, tax, and advisory services.
November 6, 2025
|

Explore the leading accounting firms in South Africa providing expert audit, tax, cloud accounting, and payroll services. Learn about their key features and unique offerings.
February 2, 2026
|
Services We Provide
Industries We Serve









.webp)