.webp)
 Cybersecurity
Cybersecurity6 Key Cybersecurity Standards: PCI DSS, HIPAA, ISO 27001, NIST, SOC 2, DORA

Content
Cybersecurity compliance is a top priority for businesses in the digital economy. According to McKinsey’s survey, 48% of companies planned to prioritize cybersecurity in 2023 and beyond. As digital operations expand, so do the risks from data breaches and reputational harm, to costly regulatory penalties.
To mitigate these challenges, businesses must align with industry-recognized compliance frameworks, such as PCI DSS, HIPAA, ISO 27001, NIST, SOC 2, and DORA. These standards provide clear, enforceable guidelines to strengthen resilience, manage risk, and demonstrate accountability.
In this article, we’ll explore six key cybersecurity compliance standards and how aligning with them can improve your organization’s security posture.
What is Cybersecurity Compliance, and Why is it Needed?
Cyber threats are rising daily, affecting not just the IT teams but also everyone connected to the organization, including vendors and customers. According to IBM’s Cost of Data Breach report 2024, the global average cost of a data breach reached $4.88 million, marking a 10% increase over the previous year and the highest on record. Business leaders increasingly recognize that to protect people and operations, robust rules and regulations must be in place. These are known as cybersecurity compliance standards.
Cybersecurity compliance is the process of ensuring that an organization adheres to established laws, regulations, and industry standards that govern the collection, storage, protection, and use of data.
For modern businesses, compliance is a strategic imperative. It protects the confidentiality, integrity, and availability of sensitive data, builds trust with customers and regulators, and reduces the risk of fines, lawsuits, and reputational damage. In simpler terms, cybersecurity compliance refers to how organizations balance operational resilience with legal accountability in a digital-first world.
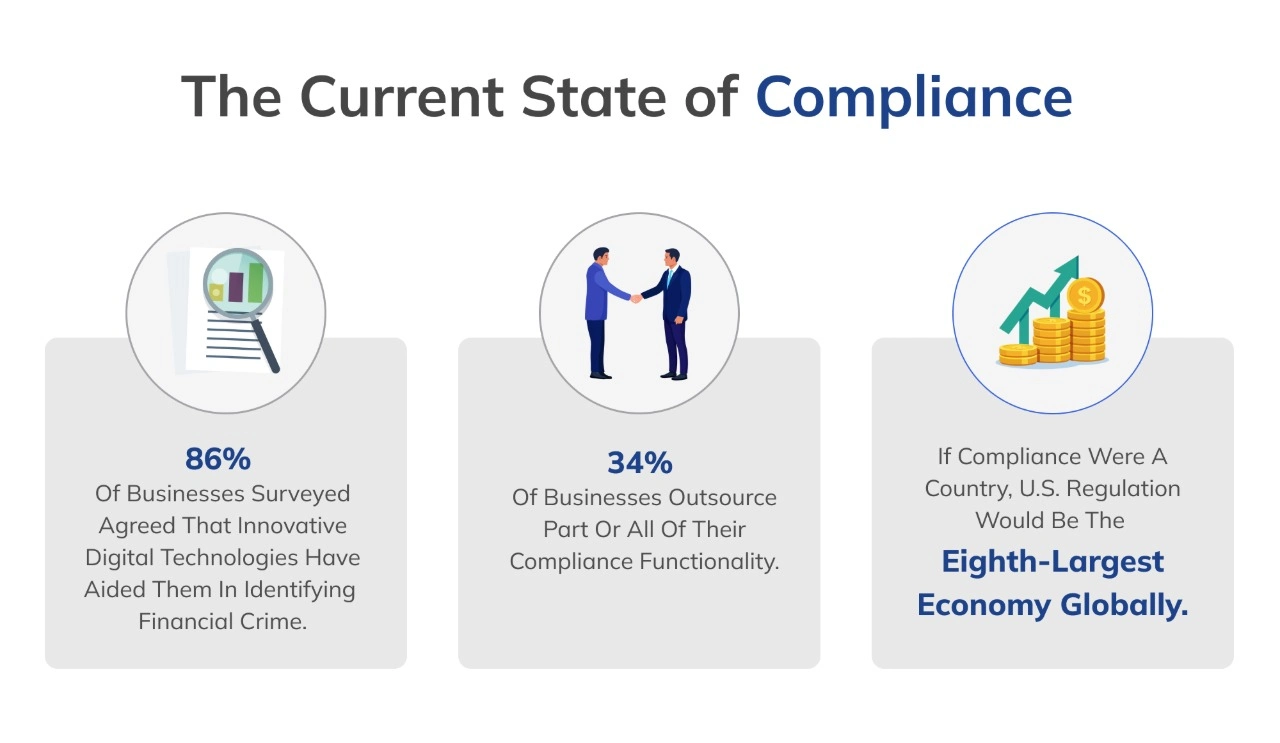
According to the IT Cybersecurity Compliance Survey conducted by Hornet Security in 2023, 79% of organizations are more concerned about compliance issues and at least 59% of the respondents feel that meeting IT compliance requirements impacts IT department's day-to-day activities.
Who Creates the Cybersecurity Frameworks You Follow?
Generally, a mix of government bodies, private organizations, and professional institutions create the cybersecurity frameworks. These frameworks help businesses meet cybersecurity compliance standards and data protection regulations.
Government institutions play a role in setting mandatory regulations. For example, HIPAA compliance requirements in healthcare are set by federal bodies to protect patient information. PCI DSS compliance checklists are overseen by regulatory authorities to ensure the secure handling of payment card data. Private organizations and professional bodies also contribute.
The National Institute of Standards and Technology, a US federal agency, develops widely adopted guidelines that many industries use to strengthen cybersecurity controls. Other frameworks, such as SOC 2, are created by industry groups to provide standards for service organizations.
Together, these bodies ensure cybersecurity frameworks remain robust, relevant, and aligned to evolving threats and regulatory demands.
What Types of Data are Subject to Cybersecurity Compliance?
The nature of this data varies across industries, and understanding its classification is essential for aligning compliance with business risk.
Executives must view compliance not as a checkbox, but as a data governance strategy, one that secures trust, ensures operational resilience, and enables regulatory readiness.
Here are the primary data categories governed by cybersecurity compliance mandates:
1. Personally Identifiable Information (PII)
PII includes any data that can identify an individual, such as names, addresses, social security numbers, or biometric data. This information is often the primary target in breaches and is strictly regulated under laws such as GDPR, CCPA, and SOC 2, which mandate how it must be collected, processed, and retained.
2. Protected Health Information (PHI)
In healthcare and life sciences, PHI encompasses everything from electronic medical records to insurance details. HIPAA governs how this data must be protected requiring encryption, access controls, and breach notification procedures to maintain patient trust and regulatory compliance.
3. Payment Card and Financial Data
Credit card numbers, bank account details, transaction records, and tax IDs fall into this category. Breaches in this area can result in significant fraud and legal liabilities. PCI DSS, SOX, and DORA are critical for businesses in finance, retail, and fintech, ensuring secure payment ecosystems and operational resilience.
4. Intellectual Property and Trade Secrets
From proprietary algorithms and product blueprints to strategic plans, intellectual property represents a company’s competitive edge. While not always governed by a single law, frameworks like ISO 27001 and NIST provide adaptable standards to protect such sensitive, high-value data from espionage and internal misuse.
Essential Cybersecurity Compliance Frameworks Explained
1. PCI DSS – Payment Card Industry Data Security Standard
The PCI DSS is a globally recognized standard designed to secure credit and debit card transactions against data theft and fraud. Any business handling credit card information must follow the PCI DSS compliance checklist to secure financial data during processing, transmission, and storage. This includes merchants, payment processors, financial institutions, and service providers. Non-compliance can result in fines, increased transaction fees, or even loss of the ability to process card payments.
Compliance helps prevent data breaches and fraud in financial transactions.
The PCI DSS standard comprises 12 core requirements, including maintaining a secure network, encrypting cardholder data, and implementing access controls. The PCI DSS compliance checklist helps organizations ensure they have robust security protocols in place across all relevant systems. Regular audits, vulnerability scans, and risk assessments are essential components of compliance.
2. HIPAA – Health Insurance Portability and Accountability Act
HIPAA is a U.S. federal law that mandates the protection of sensitive patient health information. It applies to covered entities such as hospitals, clinics, insurers, and their business associates, including IT vendors and cloud service providers. HIPAA ensures that patients' electronic health records (EHRs) are kept confidential and secure, both in storage and in transit.
HIPAA compliance encompasses two key rules: the Privacy Rule, which governs the use and disclosure of protected health information (PHI), and the Security Rule, which outlines administrative, physical, and technical safeguards. Violations can result in fines ranging from thousands to millions of dollars, depending on the severity. Using a HIPAA compliance checklist helps healthcare providers mitigate risks and meet regulatory expectations.
3. ISO 27001 – Information Security Management Standard
ISO 27001 is an international standard published by the International Organization for Standardization (ISO) that outlines the procedures for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). It’s applicable across industries and especially valued by organizations looking to demonstrate a proactive approach to data protection.
The certification process involves rigorous audits and thorough documentation of risk management practices, security policies, incident response procedures, and ongoing continuous improvement. By following the ISO 27001 audit process, businesses can establish a framework for identifying vulnerabilities, mitigating threats, and demonstrating to clients and regulators that information security is a top priority.
4. NIST – National Institute of Standards and Technology Frameworks
The NIST Cybersecurity Framework (CSF) provides guidelines, best practices, and standards to help organizations effectively manage cybersecurity risks. Though originally designed for critical infrastructure, it has since been adopted widely across public and private sectors. Unlike other frameworks, NIST is flexible and voluntary, making it useful for tailoring cybersecurity programs to fit an organization's size and risk profile.
The core functions of the NIST framework, Identify, Protect, Detect, Respond, and Recover offer a systematic approach to enhancing resilience. Many U.S. federal agencies and government contractors use NIST guidelines as a benchmark. Aligning with NIST cybersecurity standards can also help businesses prepare for certifications like FedRAMP or SOC 2.
5. SOC 2 – Service Organization Control 2
SOC 2 is an auditing framework developed by the American Institute of Certified Public Accountants (AICPA) that evaluates a company's handling of customer data. It’s specifically relevant for SaaS providers, cloud service vendors, and IT-managed service providers. SOC 2 audits assess controls based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
A SOC 2 Type I report evaluates controls at a specific point in time, while a Type II report assesses their operational effectiveness over a period. While not a regulatory requirement, SOC 2 is often a commercial necessity; clients expect it as proof of strong internal governance and secure data management practices.
6. DORA – Digital Operational Resilience Act
DORA is a relatively new regulation from the European Union, aimed specifically at enhancing the cybersecurity and operational resilience of financial institutions. It responds to growing digital threats in finance and applies to banks, insurers, investment firms, and ICT third-party service providers operating in the EU. Companies that provide technology or cloud services often use SOC 2 reports to demonstrate strong internal controls and meet cybersecurity compliance expectations from clients.
DORA mandates comprehensive risk assessments, incident response planning, and mandatory testing of ICT systems. It also introduces strict rules for third-party ICT risk management, requiring contractual clarity and oversight. With DORA set to be fully enforced by 2026, compliance now is critical for financial institutions to avoid regulatory penalties and disruption.
Key Cybersecurity Compliance Frameworks
Why Outsourcing Cybersecurity Compliance Makes Sense
Managing cybersecurity compliance internally is a significant challenge for many organisations. The rapidly changing regulatory landscape necessitates ongoing updates to policies, continuous monitoring of security controls, and thorough documentation to meet standards such as PCI DSS, HIPAA, ISO 27001, NIST, SOC 2, and DORA.
This demands specialisation, time, and resources, often stretching IT and compliance teams too thin. Moreover, staying ahead of sophisticated cyber threats while preparing for complex audits can overwhelm internal teams, leading to non-compliance and potential penalties.
Given these complexities, outsourcing cybersecurity compliance has become a smart and efficient solution. Partnering with a compliance BPO provider allows organisations to access expert knowledge, advanced security tools, and dedicated resources without the overhead of building in-house capabilities.
Invensis Technologies exemplifies this approach by offering comprehensive, end-to-end cybersecurity compliance services to cater to diverse industry needs. Their expertise spans vulnerability assessments, policy development, employee training, continuous monitoring, and audit support, helping clients maintain robust security postures while ensuring compliance with regulatory requirements. By partnering with Invensis as a trusted compliance partner, organisations can reduce costs, mitigate risks, and focus on their core business objectives with confidence.
Conclusion
By conducting risk assessments, training employees, and regularly auditing security practices, companies can stay ahead of threats and avoid costly penalties. Prioritizing compliance is not just a legal obligation; it’s a strategic advantage in ensuring trust with customers and partners.
Hence, ensure your business meets all cybersecurity compliance requirements with expert support from Invensis.
Our tailored solutions help you implement robust security measures that safeguard your data and operations. Contact Invensis today to discover how we can enhance your cybersecurity compliance and mitigate risk.
FAQs: Understanding Key Cybersecurity Compliance Standards
Discover Our Full Range of Services
Click HereExplore the Industries We Serve
Click HereBlog Category
Related Articles

Optimize your store in 2026 with the best WooCommerce order management plugins. Automate order tracking, inventory, and customer service for success.
January 21, 2026
|

Find the leading accounting firms in Singapore trusted by businesses for audit, tax, and advisory services.
November 6, 2025
|

Explore the leading accounting firms in South Africa providing expert audit, tax, cloud accounting, and payroll services. Learn about their key features and unique offerings.
February 2, 2026
|
Services We Provide
Industries We Serve





.webp)
.webp)